Protecting your IP (Intellectual Property) by securing your production at contract manufacturers
In our Secure Production webinar, we cover the following to ensure your intellectual property is protected during production runs at contract manufacturers: Mutual authentication, authorization, confidentiality
Overview: Solid Protection for IP
When bringing a new product to market, many will employ a contract manufacturer (CM) to help with mass production. This means they get access to your intellectual property (IP), including large quantities of components which they’ve been contracted to produce.
With these valuable resources in someone else’s hands, it only makes sense that you still maintain full control over your IP and to limit CM production volume. It is the most secure way to prevent potential theft, cloning and revenue loss.
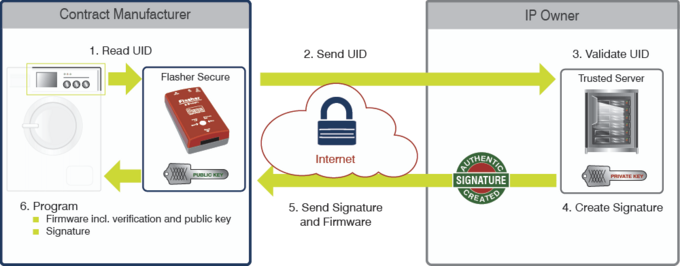
This is where SEGGER can help, by offering tried-and-tested tools such as the Flasher Secure production programmer and emSecure software solution for embedded devices. To combat these threats, Flasher Secure uses mutual authentication, authorization, and confidentiality to secure your IP and production run. As an IP owner, you have full end-to-end control of your production chain.
Flasher Secure — The Flash Programmer for Authenticated Production
The mass production programming Flasher Secure is the ideal solution for protecting a vendor’s intellectual property in any production site. Vendors keep full control over programming processes when outsourcing to CMs, and in similar environments.
CM administration & setup portal, ultra-fast programming, counterfeit unit production prevention and support for Cortex-M, RX & PPC are just some of its features.
emSecure — Create and Verify Digital Signatures
The emSecure solution enables the secure authentication of digital assets. Products can be protected from cloning and hacking at no unit cost.
The highest portability with a very small memory footprint make emSecure the ideal cryptographic solution. Its algorithms are designed to suit different needs and meet important cryptographic requirements. Thanks to its powerful API, users can easily integrate it into existing applications while a key generator and tools round off this complete security package.
Learn more about emSecure here.